Cryptography 2 Lecture Flashcards
Pinned to
8
0
0
No tags specified
|
|
Created by sss tttttt
over 6 years ago
|
|
Close
|
|
Created by sss tttttt
over 6 years ago
|
|

What is the importance of models and definitions?
What do threat models and security definitions enable?
What does a "clear" threat model and security definition allow?
A clear threat model and security definition enables...
Cryptography currently requires 4 computational assumptions, one of which is...
(1)
Cryptography currently requires 4 computational assumptions, which are...
(2)
Cryptography currently requires 4 computational assumptions, which are...
(3)
Cryptography currently requires 4 computational assumptions, which are...
(4)
Skytale is an example of a...
In a transposition cipher, what is kept the same and what is changed?
The Caesar cipher is an example of a...
In a substitution cipher, what is kept the same and what is changed?
When using modular arithmetic what are we looking for?
8 mod 3 = ?
means...

(CAN...)

The caesar cipher has a shift amount of...
25 = 35 mod 10
why is this correct?
25 != (35 mod 10)
why is this correct?
5 = (35 mod 10)
why is this correct?
Ring of Congruence Example
[3] + [4] = [7] = [2]
{... -8, -3, 2, 7 ... }
What is the significance of Z5?
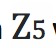
ROT13 is an X that has a key of Y
The Vigenere cipher is...
The Vigenere cipher applies...

 Hide known cards
Hide known cards