Close

A VLAN creates a logical broadcast domain that can span multiple physical LAN segments. VLANs improve network performance by separating large broadcast domains into smaller ones.
If a device in one VLAN sends a broadcast Ethernet frame, all devices in the VLAN receive the frame, but devices in other VLANs do not
The primary benefits of using VLANs are as follows:
* Security - Groups that have sensitive data are separated from the rest of the network, decreasing the chances of confidential information breaches.
* Cost reduction - Cost savings result from reduced need for expensive network upgrades and more efficient use of existing bandwidth and uplinks
* Better performance - Dividing flat Layer 2 networks into multiple logical workgroups (broadcast domains) reduces unnecessary traffic on the network and boosts performance
1. Data VLAN - is common practice to separate voice and management traffic from data traffic. A data VLAN is sometimes referred to as a user VLAN. Data VLANs are used to separate the network into groups of users or devices.
4. A management VLAN - is any VLAN configured to access the management capabilities of a switch. VLAN 1 is the management VLAN by default
3. A native VLAN is assigned to an 802.1Q trunk port.
Trunk ports are the links between switches that support the transmission of traffic associated with more than one VLAN.
An 802.1Q trunk port supports traffic coming from many VLANs (tagged traffic), as well as traffic that does not come from a VLAN (untagged traffic)
VLAN 1
* All ports assigned to VLAN 1 to forward data by default.
* Native VLAN is VLAN 1 by default.
* Management VLAN is VLAN 1 by default.
* VLAN 1 cannot be renamed or deleted.
A separate VLAN is needed to support Voice over IP (VoIP). VoIP traffic requires:
* Assured bandwidth to ensure voice quality
* Transmission priority over other types of network traffic
* Ability to be routed around congested areas on the network
* Delay of less than 150 ms across the network
A VLAN trunk extends VLANs across an entire network. Cisco supports IEEE 802.1Q for coordinating trunks on Fast Ethernet, Gigabit Ethernet, and 10-Gigabit Ethernet interfaces.
VLAN trunks allow all VLAN traffic to propagate between switches, so that devices which are in the same VLAN, but connected to different switches, can communicate without the intervention of a router.
The 802.1Q header includes a 4-byte tag inserted within the original Ethernet frame header, specifying the VLAN to which the frame belongs.
When the switch receives a frame on a port configured in access mode and assigned a VLAN, the switch inserts a VLAN tag in the frame header, recalculates the FCS, and sends the tagged frame out of a trunk port.
802.1Q header- VLAN Tag Field Details
* Type - A 2-byte value called the tag protocol ID (TPID) value. For Ethernet, it is set to hexadecimal 0x8100.
* User priority - A 3-bit value that supports level or service implementation.
* Canonical Format Identifier (CFI) - A 1-bit identifier that enables Token Ring frames to be carried across Ethernet links.
* VLAN ID (VID) - A 12-bit VLAN identification number that supports up to 4096 VLAN IDs.
When configuring an 802.1Q trunk port, a default Port VLAN ID (PVID) is assigned the value of the native VLAN ID. All untagged traffic coming in or out of the 802.1Q port is forwarded based on the PVID value.
The Cisco IP Phone contains an integrated three-port 10/100 switch. The ports provide dedicated connections to these devices:
* Port 1 connects to the switch or other VoIP device.
* Port 2 is an internal 10/100 interface that carries the IP phone traffic.
* Port 3 (access port) connects to a PC or other device.
The number of supported VLANs is large enough to accommodate the needs of most organizations.
For example, the Catalyst 2960 and 3560 Series switches support over 4,000 VLANs. Normal range VLANs on these switches are numbered 1 to 1,005 and extended range VLANs are numbered 1,006 to 4,094
Normal Range VLANs
* Used in small- and medium-sized business and enterprise networks.
* Identified by a VLAN ID between 1 and 1005.
* IDs 1002 through 1005 are reserved for Token Ring and FDDI VLANs.
Extended Range VLANs
* Enable service providers to extend their infrastructure to a greater number of customers. Some global enterprises could be large enough to need extended range VLAN IDs.
* Are identified by a VLAN ID between 1006 and 4094.
* Configurations are not written to the vlan.dat file.
When configuring normal range VLANs, the configuration details are stored in flash memory on the switch in a file called vlan.dat.
Flash memory is persistent and does not require the "copy running-config startup-config" command.
use the following command to create VLANs 100, 102, 105, 106, and 107:
"S1(config)# vlan 100, 102, 105-107 "
The "switchport mode access" command is optional, but strongly recommended as a security best practice. With this command, the interface changes to permanent access mode.
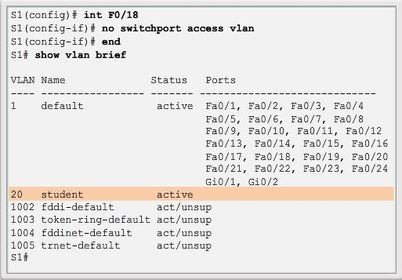
The "switchport access" vlan command forces the creation of a VLAN if it does not already exist on the switch. For example, VLAN 30 is not present in the "show vlan brief" output of the switch. If the "switchport access vlan 30" command is entered on any interface with no previous configuration, then the switch displays the following:
% Access VLAN does not exist. Creating vlan 30
Caution: Before deleting a VLAN, be sure to first reassign all member ports to a different VLAN. Any ports that are not moved to an active VLAN are unable to communicate with other hosts after the VLAN is deleted and until they are assigned to an active VLAN.
Note: For a Catalyst switch, the "erase startup-config" command must accompany the "delete vlan.dat" command prior to reload to restore the switch to its factory default condition.


With this command, the interface changes to permanent trunking mode.
The port enters into a Dynamic Trunking Protocol (DTP) negotiation to convert the link into a trunk link even if the interface connecting to it does not agree to the change
Note: This configuration assumes the use of Cisco Catalyst 2960 switches which automatically use 802.1Q encapsulation on trunk links. Other switches may require manual configuration of the encapsulation. Always configure both ends of a trunk link with the same native VLAN. If 802.1Q trunk configuration is not the same on both ends, Cisco IOS Software reports errors.
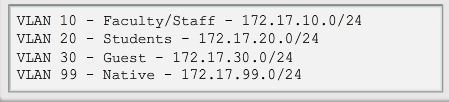
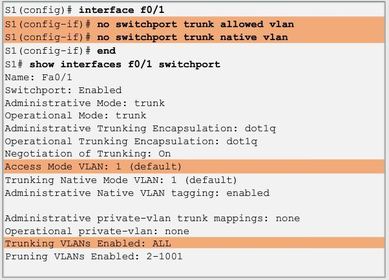
Verifying Trunk Configuration
Trunk negotiation - is managed by the Dynamic Trunking Protocol (DTP),
Which operates on a point-to-point basis only, between network devices.
DTP is a Cisco proprietary protocol that is automatically enabled on Catalyst 2960 and Catalyst 3560 Series switche DTP manages trunk negotiation only if the port on the neighbor switch is configured in a trunk mode that supports DTP.
* Switchport mode access
Puts the interface (access port) into permanent nontrunking mode and negotiates to convert the link into a nontrunk link. The interface becomes a nontrunk interface, regardless of whether the neighboring interface is a trunk interface.
* switchport mode dynamic auto - Makes the interface able to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk or desirable mode.
The default switchport mode for all Ethernet interfaces is "dynamic auto"
* switchport mode trunk
Puts the interface into permanent trunking mode and negotiates to convert the neighboring link into a trunk link.
The interface becomes a trunk interface even if the neighboring interface is not a trunk interface.
To determine the current DTP mode, issue the "show dtp interface" command
* Note: A general best practice is to set the interface to trunk and nonegotiate when a trunk link is required. On links where trunking is not intended, DTP should be turned off.
Step 1. Use the show vlan command to check whether the port belongs to the expected VLAN. If the port is assigned to the wrong VLAN, use the switchport access vlan command to correct the VLAN membership. Use the show mac address-table command to check which addresses were learned on a particular port of the switch and to which VLAN that port is assigned.
Step 2. If the VLAN to which the port is assigned is deleted, the port becomes inactive. Use the show vlan or show interfaces switchport command.
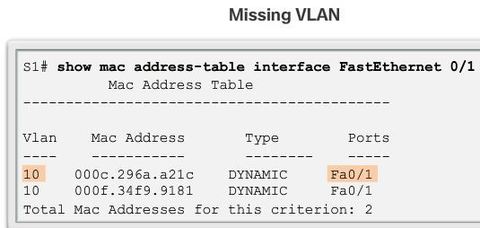
Troubleshooting Trunks
Step 1. Use the show interfaces trunk command to check whether the local and peer native VLANs match. If the native VLAN does not match on both sides, VLAN leaking occurs.
Step 2. Use the show interfaces trunk command to check whether a trunk has been established between switches. Statically configure trunk links whenever possible. Cisco Catalyst switch ports use DTP by default and attempt to negotiate a trunk link.
CDP displays a notification of a native VLAN mismatch on a trunk link with this message:
*Mar 1 06:45:26.232: %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on FastEthernet0/1 (2), with S2 FastEthernet0/1 (99).
If an issue with a trunk is discovered and if the cause is unknown, start troubleshooting by examining the trunks for a native VLAN mismatch.
If that is not the cause, check for trunk mode mismatches, and finally check for the allowed VLAN list on the trunk
Trunk Mode Mismatches
Examining the F0/3 interface reveals that the switch port is actually in dynamic auto mode. An examination of the trunks on switch S3 reveals that there are no active trunk ports.
Further checking reveals that the Fa0/3 interface is also in dynamic auto mode. This explains why the trunk is down.
To resolve the issue, reconfigure the trunk mode of the F0/3 ports on switches S1 and S3
. Switch spoofing is a type of VLAN hopping attack that works by taking advantage of an incorrectly configured trunk port. By default, trunk ports have access to all VLANs and pass traffic for multiple VLANs across the same physical link, generally between switches
In a basic switch spoofing attack, the attacker takes advantage of the fact that the default configuration of the switch port is dynamic auto. The network attacker configures a system to spoof itself as a switch.
This tag allows the frame to be forwarded to a VLAN that the original 802.1Q tag did not specify. An important characteristic of the double-encapsulated VLAN hopping attack is that it works even if trunk ports are disabled, because a host typically sends a frame on a segment that is not a trunk link.
The best approach to mitigating double-tagging attacks is to ensure that the native VLAN of the trunk ports is different from the VLAN of any user ports
The PVLAN Edge feature has the following characteristics:
* A protected port does not forward any traffic (unicast, multicast, or broadcast) to any other port that is also a protected port, except for control traffic. Data traffic cannot be forwarded between protected ports at Layer 2.
* Forwarding behavior between a protected port and a nonprotected port proceeds as usual.
* Protected ports must be manually configured.

There are many key structures and performance-related characteristics referred to when discussing networks:
* Topology - There are physical and logical topologies.
* Speed - Speed is a measure of the data rate in bits per second (b/s) of a given link in the network.
* Cost - Cost indicates the general expense for purchasing of network components, and installation and maintenance of the network.
* Security - Security indicates how protected the network is, including the information that is transmitted over the network.
* Process switching - An older packet forwarding mechanism still available for Cisco routers. When a packet arrives on an interface, it is forwarded to the control plane where the CPU matches the destination address with an entry in its routing table, and then determines the exit interface and forwards the packet.
It is important to understand that the router does this for every packet, even if the destination is the same for a stream of packets. This process-switching mechanism is very slow and rarely implemented in modern networks
* Fast switching - This is a common packet forwarding mechanism which uses a fast-switching cache to store next-hop information. When a packet arrives on an interface, it is forwarded to the control plane where the CPU searches for a match in the fast-switching cache. If it is not there, it is process-switched and forwarded to the exit interface
* Cisco Express Forwarding (CEF) - Like fast switching, CEF builds a Forwarding Information Base (FIB), and an adjacency table. However, the table entries are not packet-triggered like fast switching but change-triggered such as when something changes in the network topology. Therefore, when a network has converged, the FIB and adjacency tables contain all the information a router would have to consider when forwarding a packet.
The FIB contains pre-computed reverse lookups, next hop information for routes including the interface and Layer 2 information. Cisco Express Forwarding is the fastest forwarding mechanism and the preferred choice on Cisco routers.
"show ip interface brief" - Displays a summary for all interfaces including the IPv4 address of the interface and current operational status.
Note: In Figure 1, the Embedded-Service-Engine0/0 interface is displayed because Cisco ISRs G2 have dual core CPUs on the motherboard.
" show ip interface" - Displays the IPv4 related information for all interfaces on a router.
" show running-config interface (interface-id) "
Displays the commands configured on the specified interface.
"show interfaces "
Displays interface information and packet flow count for all interfaces on the device.
The "show ipv6 interface brief" command in Figure 1 displays a summary for each of the interfaces. The [up/up] output on the same line as the interface name indicates the Layer 1/Layer 2 interface state. This is the same as the Status and Protocol columns in the equivalent IPv4 command.
The other address, which begins with FE80, is the link-local unicast address for the interface
The "show ipv6 interface gigabitethernet 0/0"
command output shown in Figure 2 displays the interface status and all of the IPv6 addresses belonging to the interface. Along with the link local address and global unicast address, the output includes the multicast addresses assigned to the interface, beginning with prefix FF02.
The "show ipv6 route" command shown in Figure 3 can be used to verify that IPv6 networks and specific IPv6 interface addresses have been installed in the IPv6 routing table.
Other useful IPv6 verification commands include:
" show interface "
" show ipv6 routers "
Filtering commands can be used to display specific sections of output. To enable the filtering command, enter a pipe (|) character after the show command and then enter a filtering parameter and a filtering expression.
* section - Shows entire section that starts with the filtering expression
" include "
Includes all output lines that match the filtering expression
"exclude "
Excludes all output lines that match the filtering expression
"begin"
Shows all the output lines from a certain point, starting with the line that matches the filtering expression
"begin"
Shows all the output lines from a certain point, starting with the line that matches the filtering expression
Router Switching Function
A key responsibility of the switching function is to encapsulate packets in the appropriate data link frame type for the outgoing data link.
Note: In this context, the term “switching” literally means moving packets from source to destination and should not be confused with the function of a Layer 2 switch.
After the router has determined the exit interface using the path determination function, the router must encapsulate the packet into the data link frame of the outgoing interface.
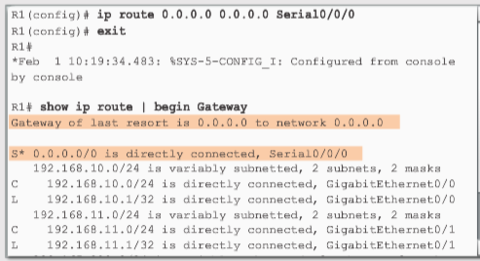
"No route determined"
If the destination IP address of the packet does not belong to either a connected or remote network, the router determines if there is a Gateway of Last Resort available. A Gateway of Last Resort is set when a default route is configured on a router. If there is a default route, the packet is forwarded to the Gateway of Last Resort. If the router does not have a default route, then the packet is discarded.
Best Path
* Routing Information Protocol (RIP) - Hop count
When a router has two or more paths to a destination with equal cost metrics, then the router forwards the packets using both paths equally.
This is called equal cost load balancing.
The routing table contains the single destination network, but has multiple exit interfaces, one for each equal cost path. The router forwards packets using the multiple exit interfaces listed in the routing table.
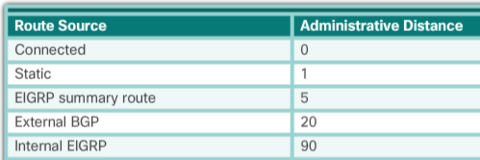
Cisco IOS uses what is known as the administrative distance (AD) to determine the route to install into the IP routing table.
The AD represents the "trustworthiness" of the route; the lower the AD, the more trustworthy the route source.
For example, a static route has an AD of 1, whereas an EIGRP-discovered route has an AD of 90.
The sources of the routing table entries are identified by a code. The code identifies how the route was learned. For instance, common codes include:
* L - Identifies the address assigned to a router’s interface. This allows the router to efficiently determine when it receives a packet for the interface instead of being forwarded.
* C - Identifies a directly connected network.
Before the interface state is considered up/up and added to the IPv4 routing table, the interface must:
* Be assigned a valid IPv4 or IPv6 address
The benefits of using static routes include improved security and resource efficiency. Static routes use less bandwidth than dynamic routing protocols, and no CPU cycles are used to calculate and communicate routes.
The main disadvantage to using static routes is the lack of automatic reconfiguration if the network topology changes.
There are two common types of static routes in the routing table:
1. Static route to a specific network
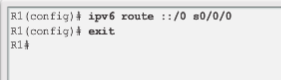
2. Default static route
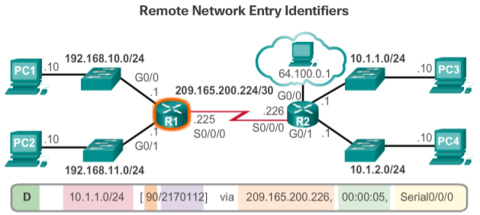
The entry beginning with ‘D*EX’ identifies that the source of this entry was EIGRP (‘D’). The route is a candidate to be a default route (‘*’), and the route is an external route (‘*EX’) forwarded by EIGRP.
The other two ‘D’ entries are routes installed in the routing table based on the update from R2 advertising its LANs.

 Hide known cards
Hide known cards