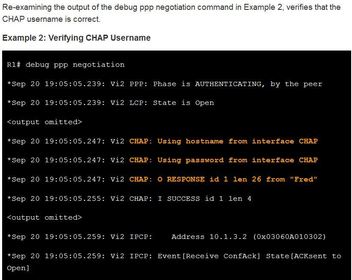
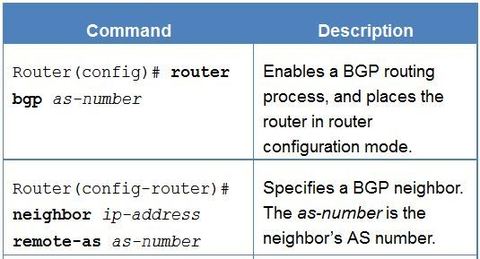
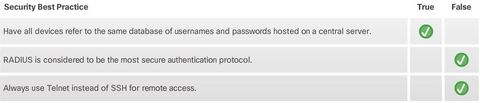
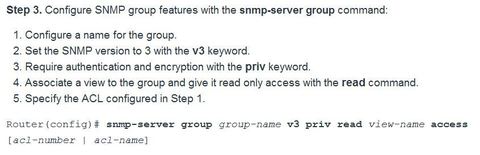
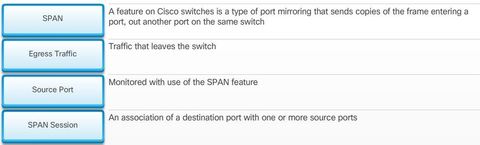
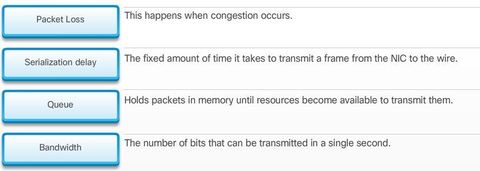
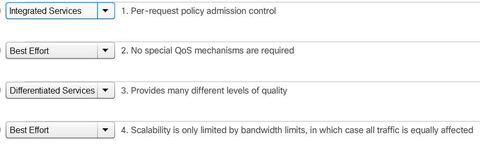
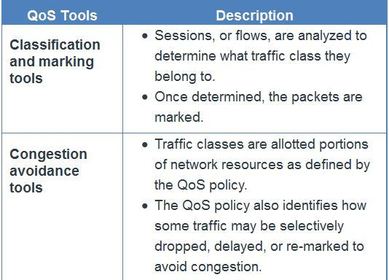
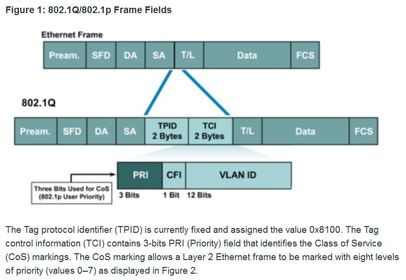
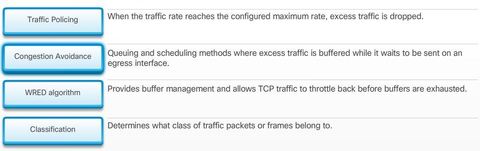
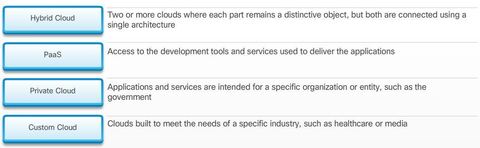
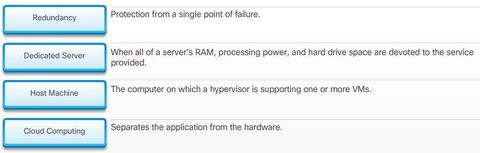
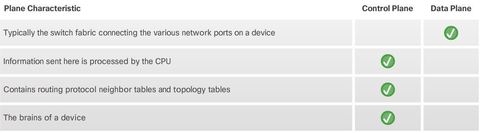
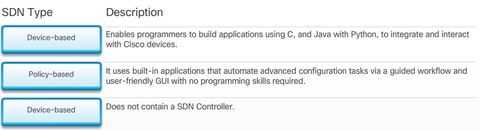
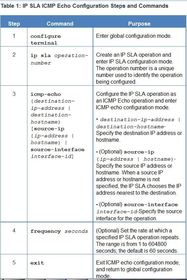
BGP, ACL IPv6, DHCP Snooping, AAA with RADIUS and TACACS+, 802.1X, SNMPv3 Conf Port Mirroring, QoS, Cloud, CEF, IP SLAs,
Pinned to
33
0
0
No tags specified
|
|
Created by John Dedios
over 8 years ago
|
|
Close